Microsoft Visio Becomes a Tool for Cybercriminals

Cybercriminals are evolving tactics, using sophisticated two-step phishing (2SP) methods that combine trusted platforms and new evasion techniques. Security researchers from Perception Point have issued a fresh warning about the rise of 2SP attacks using Microsoft Visio (.vsdx) files to bypass detection and steal credentials. This strategy underscores the increasing complexity of phishing attacks, targeting unsuspecting users with familiarity and deception.
Here’s how these attacks unfold and how individuals and organizations can safeguard against them.
What Are Two-Step Phishing Attacks?
Two-step phishing attacks are advanced cybercrime strategies designed to evade traditional email security measures. Unlike standard phishing emails that directly lure victims into compromising their credentials, 2SP attacks add layers of obfuscation, making detection far more challenging.
In these attacks, the initial email comes from a breached but legitimate email account, ensuring it passes basic authentication checks. This adds an air of credibility, increasing the likelihood that recipients will engage with the content. The email includes an enticing call to action, a seemingly harmless request to review a business proposal or respond to an urgent purchase order. Clicking the provided link directs the recipient to a compromised platform, such as Microsoft SharePoint, hosting the malicious Visio (.vsdx) file.
This deliberate human interaction bypasses many detection systems, redirecting the victim to a fake Microsoft 365 login page. The final step: users are tricked into entering their login credentials on the fake portal, and handing over sensitive information to the attackers.
Microsoft Visio Files as a Phishing Tool
The use of Microsoft Visio files represents a new frontier in phishing attacks. Visio is widely used in workplaces for creating diagrams, workflows, and visual data representations, making it an ideal tool for threat actors exploiting “harmless familiarity.”
The researchers at Perception Point identified a sharp increase in attacks leveraging .vsdx files. These files, embedded with malicious URLs, serve as the bait in a multi-layered phishing scheme. The attack unfolds as follows:
- Initial Lure: A legitimate-looking email containing a link to a Visio file hosted on a compromised platform.
- Embedded URL: The Visio file contains a clickable call-to-action, such as a “view document” button, which links to a fake login page.
- Human Interaction: Victims are instructed to hold down the Ctrl key while clicking the link, a tactic designed to bypass automated security scanners.
- Credential Theft: The final step redirects victims to a convincing Microsoft 365 login page that captures their credentials.
These 2SP attacks highlight how cybercriminals continually adapt their methods to outsmart security systems. By embedding malicious URLs in trusted file formats like .vsdx, attackers exploit both technical vulnerabilities and human psychology. The reliance on human interaction—asking users to hold down the Ctrl key—demonstrates the sophistication of these attacks. Automated detection tools often fail to flag such behavior, leaving individuals and organizations vulnerable.
Why Email Security Is Crucial
At the core of these attacks is the exploitation of email systems. Breached email accounts are used to distribute phishing messages that appear credible to recipients, bypassing traditional authentication checks. This layer of authenticity makes it easier for attackers to lure victims into their traps. This makes robust email security an essential line of defense.
Organizations must implement advanced email filtering solutions capable of detecting unusual patterns, such as sudden spikes in outbound messages from a single account. Regular monitoring and rapid response protocols are critical to mitigating the risks posed by compromised accounts.
Steps to Mitigate Two-Step Phishing Attacks
Given the sophistication of these 2SP attacks, traditional security measures are no longer sufficient. Here are key steps to protect against them:
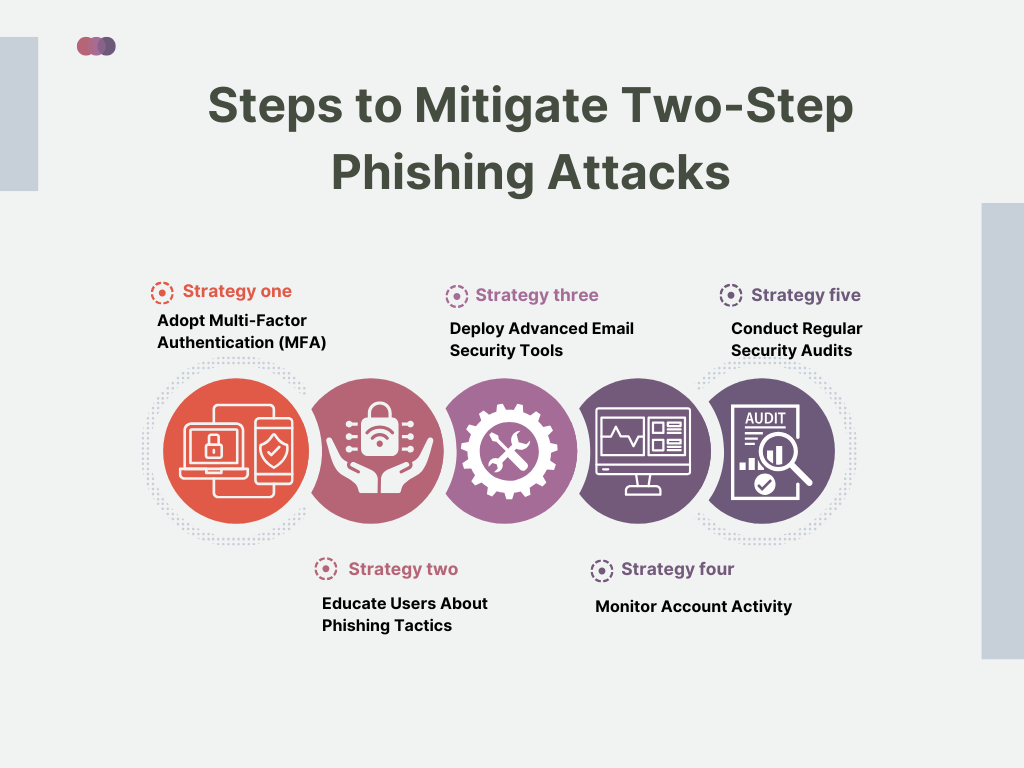
1. Adopt Multi-Factor Authentication (MFA)
- MFA provides an additional layer of security by requiring users to verify their identity through a secondary method, such as a mobile app or biometric data.
- Even if attackers steal credentials, MFA can prevent unauthorized access.
2. Educate Users About Phishing Tactics
- Regular training sessions can help employees recognize phishing attempts, including unusual requests like holding down the Ctrl key to click a link.
- Foster a culture of caution, encouraging users to verify suspicious emails before engaging.
3. Deploy Advanced Email Security Tools
- Use email security solutions that can detect and block phishing attempts, even when embedded in trusted file formats.
- Enable automated scanning of email attachments and URLs to identify potential threats.
4. Monitor Account Activity
- Implement tools to track login patterns and flag unusual activity, such as logins from unfamiliar locations or devices.
- Act swiftly to secure compromised accounts.
5. Conduct Regular Security Audits
- Regularly review security protocols and update systems to address emerging threats.
- Test the organization’s ability to detect and respond to phishing attacks through simulated phishing exercises.
The Importance of Proactive Security
As cybercriminals become more innovative, businesses and individuals must stay one step ahead. The rise of 2SP attacks using Microsoft Visio files underscores the need for proactive security measures. These attacks exploit the trust placed in familiar tools and processes, emphasizing the importance of vigilance and robust defense strategies.
By combining advanced technologies like AI-driven threat detection with user education and strong authentication practices, organizations can create a resilient defense against even the most sophisticated threats.
Looking Ahead
The increasing prevalence of two-step phishing attacks highlights a critical shift in cybercrime tactics. Attackers are not just targeting technical vulnerabilities—they are exploiting human behavior and trusted platforms to achieve their goals. As we move forward, organizations must recognize that layered security strategies are essential. Protecting against these advanced threats requires a holistic approach that combines technology, training, and vigilance.
By staying informed about emerging threats and adopting proactive measures, businesses can safeguard their data, protect their users, and maintain trust in an increasingly digital world. Subscribe to our newsletter now to stay ahead!
FAQs
1. What are these new cyber attacks using Visio files?
Cybercriminals are using Microsoft Visio (.vsdx) files in phishing attacks. These files embed malicious URLs designed to steal user credentials.
2. How do these Visio-based phishing attacks work?
Victims receive emails with links to Visio files hosted on compromised platforms. Clicking the embedded URLs redirects them to fake login pages to steal credentials.
3. Why are Visio files being used for phishing?
Visio files are trusted in workplaces, making them ideal for deceptive attacks. This “harmless familiarity” helps bypass user suspicion and some security systems.
4. How can I protect myself from these attacks?
Enable multi-factor authentication (MFA), avoid clicking links in unexpected emails, and ensure your email security systems are up-to-date.




