Optimize Cybersecurity Programs with Leading Frameworks

In today's digital landscape, the rising frequency and sophistication of cyber threats demand robust cybersecurity measures. Organizations must effectively manage risks, protect sensitive data, and ensure operational continuity. Cybersecurity frameworks provide a structured approach to building and optimizing cybersecurity programs. These frameworks, such as the NIST Cybersecurity Framework and ISO 27001 for data protection, offer best practices for addressing vulnerabilities, implementing controls, and ensuring compliance. By leveraging cybersecurity frameworks, businesses can systematically strengthen their security posture, align with industry standards, and optimize their cybersecurity program for long-term resilience. These frameworks help organizations manage risk while ensuring business continuity in an increasingly complex environment.
Why Should You Use a Cybersecurity Framework?
Cybersecurity frameworks are a great requirement in providing building blocks for organizations who want to develop secure security programs and protect their digital assets regrowth. Using frameworks such as the NIST Cybersecurity Framework or even ISO 27001 for data protection, organizations can show a commitment to cybersecurity best practices. These frameworks not only help address regulatory compliance but also strengthen resilience by empowering firms to promptly and effectively contain, respond to, and recover from a cyber incident. Having such frameworks in place instills trust among your stakeholders, conveying the message that your organization cares about protecting sensitive data. And frameworks, that lend themselves to a more methodical process of refining a cybersecurity program by ensuring iterative improvement. Cybersecurity frameworks help organizations comply with legal standards, but the benefits go beyond compliance; they enable organizations to mitigate ever-evolving cyber threats and ensure business continuity.
Key Cybersecurity Frameworks to Know and Use
When building a robust cybersecurity program, leveraging established cybersecurity frameworks is essential for optimizing your defenses. Here are four key frameworks to consider:
NIST Cybersecurity Framework (CSF)
Purpose: A flexible, widely adopted framework applicable across various sectors.
Benefits: Supports continuous improvement and resilience, enhancing your ability to manage cyber risks and recover from incidents.
ISO/IEC 27001
Purpose: A globally recognized standard for information security management.
Benefits: Aids in improving risk management and ensures compliance with international data protection regulations.
CIS Controls
Purpose: A set of prioritized security measures for organizations of all sizes.
Benefits: Ideal for small and mid-sized businesses seeking clear, actionable cybersecurity best practices.
COBIT (Control Objectives for Information and Related Technologies)
Purpose: Aligns cybersecurity goals with business objectives.
Benefits: Provides governance for enterprise-level organizations, helping bridge the gap between IT and business operations
Steps to Implement a Cybersecurity Framework
Implementing a cybersecurity framework is essential for optimizing security programs and protecting valuable data. Here’s a step-by-step guide to help you get started:
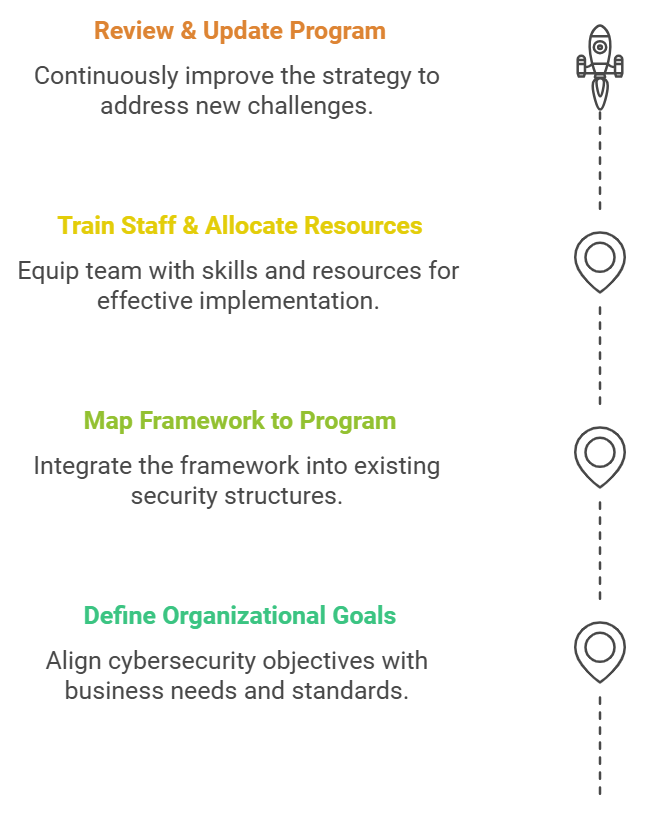
1. Assess your current security posture: Start by assessing the current security infrastructures in place. Determine any strong points, weak points, and deficiencies to assess areas that require advancement. This is important in ensuring the reframing of the approach is done smartly.
2. Define goals based on organizational needs: Matrix the framework to the business requirements. Be it the data in ISO 27001 or the protection of infrastructure in NIST standards, emphasizing specific targets is fundamental in making sure the framework adapts adequately to the requirements.
3. Map the framework to your existing program: All the essential elements of the framework should be incorporated into the existing structural measures taken to combat cybersecurity threats. This facilitates integration and avoids the need for new measures without compromising the current structures.
4. Train staff and allocate resources: Equip your team with the appropriate skills and information. Engaging employees in needed training related to cyber threat prevention is a determinant in the proper securing of the environment.
5. Regularly review and update the program: Address modern challenges by revisiting old threats and incorporating them into your cybersecurity strategy that is sufficiently comprehensive to counter new challenges.
By following these steps, you can effectively implement and optimize cybersecurity frameworks, ensuring robust protection and compliance.
Building an Optimized Cybersecurity Program
Optimizing an efficient cybersecurity program requires a level of planning directed toward hardware and other valuable assets that are highly critical to the organization. Begin assessing risk – assess the locations of highest risk and value. NIST Cybersecurity Framework and ISO 27001, both of which are cybersecurity frameworks for data protection, help organizations in the effective management of risk by taking them through structured processes that appear to be best practices. Integrate several automation systems such as artificial intelligence and machine learning to streamline the process of incident detection and response. Ensure an effective incident response strategy is in place so that the team is equipped with the necessary tactics to handle breaches. Finally, implement organizational policies that endorse the promotion of security awareness and accountability. Such methods of program optimization have many advantages including enhanced efficiency, risk management, and compliance.
The Benefits of a Framework-driven Cybersecurity Program
There are some major benefits to having a framework–driven cybersecurity program, which is as follows:
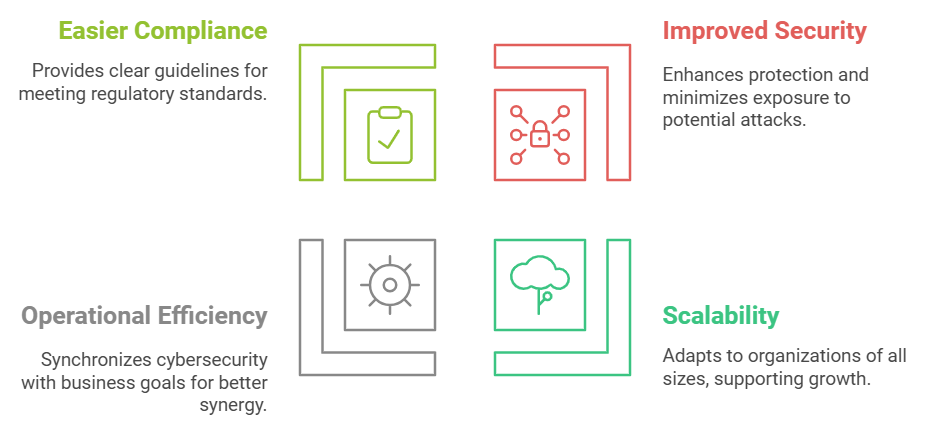
Improved Security: Cybersecurity Frameworks, such as NIST and ISO 27001 offer proven strategies for increasing protection and enabling organizations to minimize exposure and the impact of potential attacks.
Scalability: It makes frameworks scalable because they can cater to organizations of all sizes. As the business scales, they give free rein to cybersecurity measures.
Bringing it all together and Keeping it steady: The frameworks bring in lots of synergy which avoids redundancy and synchronizes the cybersecurity mechanisms with holistic business goals helping you to capitalize on operational efficiency.
Easier Compliance: With clear guidelines, frameworks make it easier to meet regulatory standards such as GDPR and HIPAA and are valuable in providing a roadmap for audits & continuous compliance.
Cybersecurity frameworks help organizations build better, scalable, efficient, and compliant cybersecurity programs.
Case Studies: Successful Implementation of Cybersecurity Frameworks
Small Business with CIS Controls: How a small business used CIS Controls to secure its network in a cost-effective manner, prioritizing affordance level protections against prevalent threats such as ransomware. Demonstrates How Security Optimizations are Possible Amidst Budget Constraints
Enterprise with NIST CSF: A cross-enterprise had implemented the NIST Cybersecurity Framework (CSF) to enhance its security program. NIST’s guidelines allowed the organization to better manage risks and compliance, providing an example of how large organizations can mature their cybersecurity capabilities
Government Agency with ISO/IEC 27001: A government agency applied ISO/IEC 27001 to improve data protection and compliance. This framework helped ensure secure data handling and meet regulatory standards.
In summary, Cybersecurity frameworks such as the National Institute of Standards and Technology (NIST), ISO 27001, or the best practices of your industry provide key structures to improve your cybersecurity program. Implementing a customized framework can help organizations strengthen and sustain their defenses, and align with mandates and regulations, while constantly evolving risk management processes. Evaluating your program against frameworks consistently makes sure it adapts to the new emerging threats keeping your data and operations secure. Adhering to cybersecurity frameworks not only protects the organizational security posture but also helps with the optimization of a cybersecurity program. Do not wait – now is the time to assess your program and embed something like ISO 27001 for data protection or the NIST cybersecurity framework so you can continuously improve and become more resilient.
Be at the forefront of technological innovation! Join our vibrant community to unlock expert insights, exclusive content, and the latest news on AI, IoT, and cutting-edge retail solutions. Stay informed, get inspired, and be part of the conversation—subscribe digitalexperience.live today for your gateway to the future!
FAQs:
1. What are the best frameworks for cybersecurity?
The best cybersecurity frameworks are NIST, ISO 27001, and CIS Controls. Thanks to these frameworks, organizations have improved security, handled the risks very well, and achieved data security and compliance with regulatory requirements.
2. What is a program framework in cybersecurity?
A cybersecurity program framework comprises best practices for the implementation of various measures to manage security such as risk assessment and risk mitigation. NIST and ISO 27001 are standard frameworks for developing resilient security programs.
3. What is optimization in cybersecurity?
Optimization in cybersecurity entails the enhancement of security measures so as to be proactive against new and emerging threats. It involves the improvement of processes, tools, and strategies for enhanced defense and compliance.
4. What are the 7 categories of the NICE cybersecurity workforce framework?
The NICE framework depicts seven categories such as Securely Provision, Operate and Maintain, Protect and Defend, Investigate, Collect And Operate, Analyze, Oversight and Develop.