US Cybersecurity Regulations: Key Insights for C-Suite

Cybersecurity regulations are legal frameworks that establish the requirements organizations must adhere to in order to safeguard their information systems, protect sensitive data, and mitigate risks associated with cyber threats and data breaches. These regulations dictate the necessary security measures, policies, and practices that organizations must implement to ensure the integrity, confidentiality, and availability of their data and the information of their customers.
The Current State of US Cybersecurity Regulations
As we enter 2024, the landscape of US cybersecurity regulations is undergoing significant transformation. Recent high-profile cyberattacks have drawn widespread attention, prompting regulatory bodies to respond with stricter guidelines. For instance, the Securities and Exchange Commission (SEC) has proposed new rules requiring public companies to disclose material cybersecurity incidents, reflecting the urgency for transparency in an era of increasing digital threats.
Additionally, the Cybersecurity and Infrastructure Security Agency (CISA) continues to enhance its framework to address emerging risks, making compliance with US cybersecurity regulations an essential focus for businesses across sectors.
Understanding the Challenges Ahead
This article will delve into the evolving US cybersecurity regulations that C-suite executives must navigate in 2024. Readers can expect an exploration of the key challenges and pain points organizations face, including the complexities of compliance, the rising costs of cyber incidents, and the need for a comprehensive cybersecurity strategy. As US cybersecurity regulations become more stringent, the stakes are high, and understanding this evolving landscape is crucial for effective risk management.
The Imperative of Compliance

The core problem at hand is the increasing complexity of US cybersecurity regulations and the corresponding need for businesses to comply with these rules while effectively managing cyber risks. With new regulations being introduced and existing laws being updated, C-suite executives are under pressure to ensure that their organizations not only meet legal obligations but also protect sensitive data from evolving cyber threats. The objective is clear: organizations must achieve compliance with US cybersecurity regulations and build a resilient cybersecurity posture to safeguard their operations and maintain stakeholder trust.
Why This Problem Matters: The Case for Action
The importance of addressing compliance with US cybersecurity regulations cannot be overstated. According to a 2023 report from the World Economic Forum, the global cost of cybercrime is projected to reach $10.5 trillion annually by 2025. This staggering figure highlights the financial implications of inadequate cybersecurity measures. Furthermore, a recent survey by Gartner revealed that 88% of boards view cybersecurity as a business risk, not just an IT issue.
Moreover, the ramifications of non-compliance with US cybersecurity regulations are severe. Organizations face significant fines, reputational damage, and the loss of customer trust. As pointed out by industry experts, including cybersecurity thought leader Bruce Schneier, “In the digital age, security is not optional; it’s a necessity.” The transition from the status quo to a proactive compliance strategy regarding US cybersecurity regulations is essential for mitigating risks and ensuring long-term business viability.
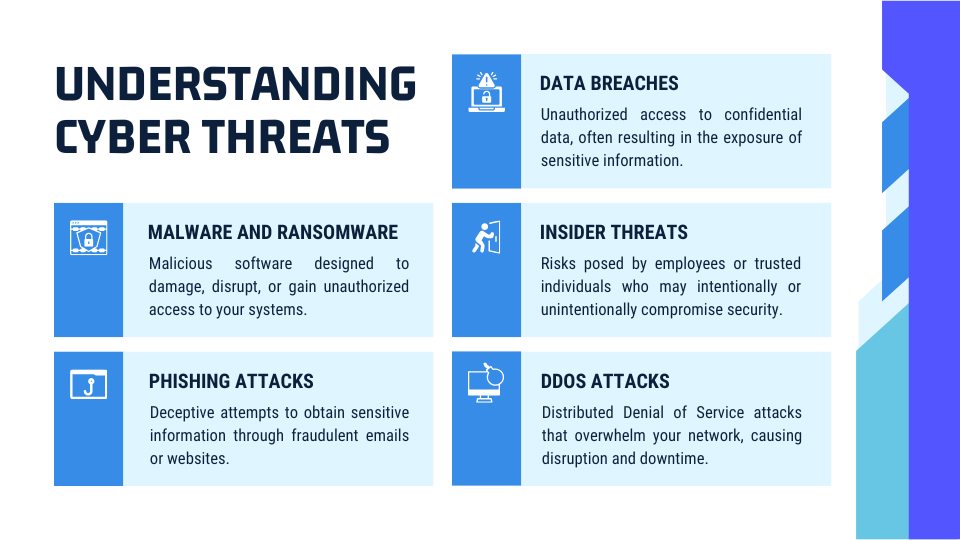
Seven Common Cybersecurity Frameworks and Standards
Organizations must prioritize robust cybersecurity practices to protect sensitive information and comply with US cybersecurity regulations. Understanding and implementing established cybersecurity frameworks and standards is crucial for achieving compliance and enhancing security posture. Here are seven common frameworks and standards that organizations should consider:
1. NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST) Cybersecurity Framework provides a flexible structure for organizations to manage and reduce cybersecurity risk. It consists of five core functions: Identify, Protect, Detect, Respond, and Recover. This framework is particularly valuable for organizations looking to align with US cybersecurity regulations while fostering a culture of security within their operations.
2. ISO 27001 and ISO 27002
ISO 27001 and ISO 27002 are international standards that provide a systematic approach to managing sensitive company information. ISO 27001 outlines the requirements for establishing, implementing, maintaining, and continually improving an information security management system (ISMS), while ISO 27002 offers best practice recommendations for information security controls. Adhering to these standards can help organizations demonstrate compliance with US cybersecurity regulations and enhance their overall security posture.
3. SOC 2
Service Organization Control 2 (SOC 2) is a framework specifically designed for service providers storing customer data in the cloud. It focuses on five trust service principles: Security, Availability, Processing Integrity, Confidentiality, and Privacy. Achieving SOC 2 compliance indicates that an organization meets high standards for protecting customer data, which aligns with the expectations set forth in US cybersecurity regulations.
4. NERC-CIP
The North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) standards are designed to secure the assets of the North American bulk power system. These standards focus on the protection of critical infrastructure and require organizations to implement security measures, conduct assessments, and maintain documentation to comply with US cybersecurity regulations in the energy sector.
5. HIPAA
The Health Insurance Portability and Accountability Act (HIPAA) establishes national standards for the protection of health information. Organizations that handle protected health information (PHI) must comply with HIPAA regulations, which mandate the implementation of security measures to safeguard sensitive data. Compliance with HIPAA is essential for organizations in the healthcare industry to meet US cybersecurity regulations.
6. GDPR
While the General Data Protection Regulation (GDPR) is an EU regulation, it has significant implications for US organizations that handle the personal data of EU citizens. GDPR mandates strict data protection and privacy measures, and organizations that fail to comply may face hefty fines. Understanding GDPR is critical for US companies operating globally to ensure they meet both GDPR and US cybersecurity regulations.
7. FISMA
The Federal Information Security Management Act (FISMA) requires federal agencies and their contractors to secure information systems. FISMA mandates a comprehensive framework for protecting government information and sets the foundation for ensuring compliance with US cybersecurity regulations across federal agencies.
These frameworks and standards provide organizations with a solid foundation for building robust cybersecurity programs that align with US cybersecurity regulations. By understanding and implementing these best practices, businesses can enhance their security posture, protect sensitive data, and mitigate risks associated with cyber threats.
How to Address the Problem: A Comprehensive Strategic Approach
To navigate the complexities of US cybersecurity regulations, businesses must adopt a holistic and multi-layered strategy that integrates regulatory compliance with operational efficiency. This strategic approach not only ensures that organizations meet regulatory requirements but also strengthens their cybersecurity posture, reducing the risk of data breaches and enhancing overall resilience. Below are the key strategic elements businesses should focus on:

1. Implementing Robust Security Frameworks
One of the most effective ways to comply with US cybersecurity regulations is by adopting established cybersecurity frameworks. These frameworks provide structured, well-defined guidelines that help organizations assess risks, implement security controls, and continuously monitor their environment. The following steps illustrate how frameworks can be implemented:
- NIST Cybersecurity Framework: This is a widely accepted framework for US organizations, offering guidance on identifying threats, protecting systems, detecting incidents, responding to breaches, and recovering from attacks. Implementing the NIST framework ensures that businesses operate within the boundaries of US cybersecurity regulations and have a standardized approach to managing cybersecurity risks.
- ISO 27001 and 27002: For businesses seeking international standards in addition to complying with US laws, ISO 27001 and ISO 27002 offer a systematic method for managing sensitive information. By developing an Information Security Management System (ISMS), organizations can integrate data protection with the demands of compliance across borders.
- SOC 2 for Cloud Security: As more companies transition to the cloud, following the SOC 2 standard for security, availability, and privacy becomes vital. This is particularly important for service providers who store and process customer data. SOC 2 compliance ensures businesses adhere to US cybersecurity regulations in the cloud environment, offering customers confidence in data security.
2. Conducting Regular Risk Assessments
Continuous risk assessments are essential for identifying vulnerabilities and ensuring that businesses remain compliant with US cybersecurity regulations as threats evolve. Organizations should establish a regular cadence of risk assessments and security audits to stay ahead of potential threats and regulatory requirements. Steps include:
- Vulnerability Scanning and Penetration Testing: Regularly test the organization’s IT infrastructure to identify weak points that could be exploited by cybercriminals. Tools such as vulnerability scanners and manual penetration testing can help uncover system weaknesses, ensuring compliance with frameworks like FISMA and NERC-CIP.
- Gap Analysis: This involves comparing your current cybersecurity practices with the requirements of the selected framework (e.g., NIST, SOC 2, or HIPAA). Conducting a gap analysis allows businesses to identify where they fall short and how they can align with US cybersecurity regulations.
- Continuous Monitoring: Industry leaders like Amazon and Microsoft advocate for continuous monitoring solutions to ensure systems are always operating within compliance guidelines. Automated tools can be used to track network activity, detect anomalies, and alert security teams in real time, preventing violations of US cybersecurity regulations.
3. Enhancing Employee Training and Awareness
Human error remains one of the leading causes of cybersecurity incidents. An effective strategy must include comprehensive training programs that educate employees about the critical role they play in maintaining cybersecurity and compliance with US cybersecurity regulations.
- Tailored Training Programs: Implement ongoing training that is specific to the frameworks in use, such as HIPAA for healthcare organizations or NERC-CIP for those in the energy sector. Each training program should emphasize the specific regulations employees need to be aware of, as well as general best practices such as password management, phishing awareness, and data encryption.
- Simulated Attacks: Companies like IBM and Acquia recommend running simulated phishing attacks and other social engineering exercises to assess employee readiness. By engaging in these simulations, employees learn how to recognize and respond to potential threats, reducing the likelihood of breaches and compliance violations.
- Building a Culture of Cybersecurity: A successful cybersecurity strategy requires a company-wide commitment to best practices. Leadership should actively promote cybersecurity initiatives, setting an example by enforcing policies and ensuring that the entire organization is aligned with US cybersecurity regulations.
4. Embracing Advanced Technologies for Compliance
Technological innovation is playing a crucial role in simplifying the complexity of complying with US cybersecurity regulations. The integration of artificial intelligence (AI), machine learning (ML), and automation tools into cybersecurity strategies can help businesses streamline processes and maintain continuous compliance. Here’s how:
- AI-Powered Threat Detection: AI can analyze vast amounts of data to identify patterns and detect anomalies that may indicate a breach. AI tools, like those used by companies such as Google and Amazon Web Services (AWS), can automatically flag suspicious activity and initiate responses to contain threats before they cause widespread damage.
- Automated Compliance Management: Tools like Compliance.ai and Drata automate the process of tracking regulatory changes, ensuring that organizations remain up-to-date with US cybersecurity regulations. These tools help reduce manual oversight and allow businesses to focus on enhancing their security measures while staying compliant.
- Zero Trust Architecture: Many organizations, including Google, are adopting a zero-trust security model, where no entity (inside or outside the network) is automatically trusted. Zero trust architectures enforce strict identity verification and continuous authentication, minimizing the risk of breaches and ensuring compliance with US cybersecurity regulations.
5. Collaboration with Industry Experts and Authorities
Compliance with US cybersecurity regulations can be complex, and businesses can benefit greatly from collaborating with external cybersecurity experts, industry groups, and regulatory authorities. This includes:
- Consulting with Experts: Engage cybersecurity consulting firms like PwC or Deloitte to ensure your cybersecurity practices align with the latest regulatory requirements and frameworks such as SOC 2, ISO 27001, and FISMA.
- Participating in Industry Coalitions: Join industry-specific cybersecurity groups, such as the Cyber Threat Alliance (CTA), to share knowledge, stay informed about emerging threats, and collaborate on best practices. Industry collaboration is crucial for staying ahead of regulatory changes and improving cybersecurity resilience.
- Engaging with Regulators: Maintain open channels of communication with regulatory bodies such as the Department of Homeland Security (DHS) and the Federal Trade Commission (FTC) to ensure you are following the most up-to-date guidance for compliance with US cybersecurity regulations.
Conclusion: Key Takeaways for C-Suite Executives

In summary, the evolving landscape of US cybersecurity regulations presents significant challenges for organizations in 2024. C-suite executives must recognize the importance of compliance with US cybersecurity regulations as a business imperative, not just a regulatory obligation. By adopting best practices and investing in a robust cybersecurity framework, along with advanced threat detection technologies, organizations can mitigate risks and safeguard their digital assets.
The benefits of addressing these challenges related to US cybersecurity regulations are manifold: enhanced compliance, reduced risk of financial loss, and improved stakeholder trust. As we navigate this complex landscape, the time for action is now. Organizations that prioritize cybersecurity will not only protect their interests but also position themselves for long-term success in an increasingly digital world.
Join our growing community at DXP.Live for more insights and resources on navigating the complex world of digital experiences and cybersecurity. Subscribe now to stay informed and empowered!
FAQs
1. What are the main cybersecurity regulations to be aware of in 2024?
Key regulations include the SEC's cyber disclosure rules and CISA's cybersecurity framework.
2. How can C-suite executives ensure compliance with cybersecurity regulations?
By conducting regular risk assessments, developing incident response plans, and investing in employee training.
3. What role does technology play in cybersecurity compliance?
Technology can automate compliance processes, enhance data protection, and provide real-time threat intelligence.
4. Why is cybersecurity a C-suite issue?
Cybersecurity impacts business strategy, risk management, and regulatory compliance, making it essential for leaders to be involved.
5. How can organizations foster a proactive cybersecurity culture?
By integrating cybersecurity into business strategy, investing in training, and encouraging collaboration between IT and leadership teams.